It’s interesting to watch who is initiating cyber-attacks against whom live, globally. Thousands of websites get hacked every day due to vulnerable files, plugins, and misconfiguration on the servers.
If you are a website owner or administrator, you can perform a security scan against your site to check vulnerabilities and malware.
Coming back to the article, if you are interested to watch attacks happening around the world, then following maps will mesmerize you.
Digital Attack Map
Watch daily DDoS attacks worldwide with Digital Attack Map. You can filter the map with multiple options.

By attacks size
- Large
- Unusual
- Combined
By attack type
- TCP Connection (filling connections)
- Volumetric (eating bandwidth)
- Fragmentation (pieces of packets)
- Application
- Source & destination port number
- Duration
DDoS is dangerous to your online business; it can take down your online presence and hurt your reputation and finances. If you are a business owner or web administrator, then you may consider protecting your online assets from DDoS by using services like SUCURI or others, as mentioned here.
Trellix
FireEye Cyber Threat Map gives you an excellent summary of total attacks today with the following data.
- Top 5 reported industries
- Top attacker by country
It’s not as detailed as one above but still useful if you are looking for data in industry and country wise.
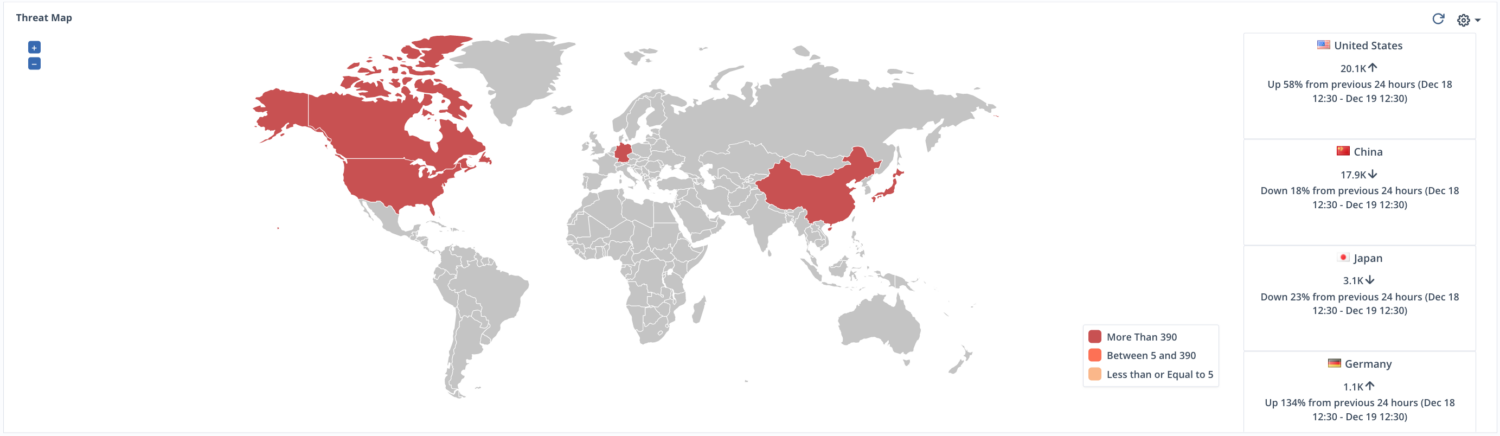
Kaspersky
Cyberthreat real-time map by Kaspersky shows you the real-time attack detected by their various source systems.
- On-Scanner access
- On-Demand Scanner
- Web Anti-virus
- Mail Anti-virus
- Intrusion Detection System
- Vulnerability Scan
- Kaspersky Anti-spam
- Botnet Activity detection

You can have data in table format under the stats page.
Threat Cloud
Threat Cloud by Check Point shows the attack data for today and yesterday. It also gives an option to view the top target and source countries.

AKAMAI
Real-time web monitor by AKAMAI shows network & attack traffic overview, which you can filter by regions.

Threatbutt
Internet attack attribution map by Threatbutt is a cool simple one.
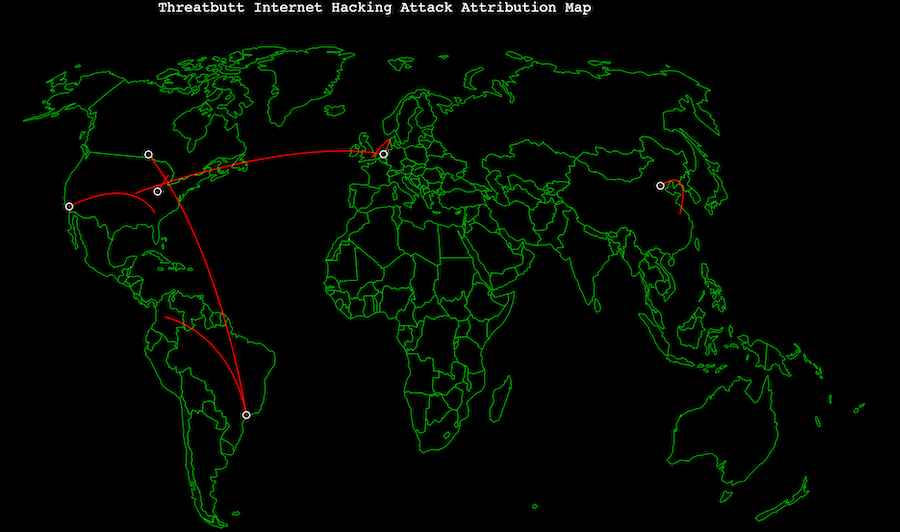
You get to see the live attack details like the software is being used to attack with the source and destination details.
FortiGuard
Real-time threat intelligence landscape by FortiGuard.
Data is from more than 2 million Fortinet products globally. You get a summary view of attack with source location and severity.
Bitdefender
There are three main types of attacks visualized on the Cyberthreat map by Bitdefender.
- Spam
- Infection
- Attack

Bitdefender is a leader in selling home and business security products.
Talos
Talos, a Cisco company, has a cyber-attack map that shows the top spam and malware senders.

Data is collected from Cisco, and third-party feeds worldwide. You can see the top 10 malware and spam senders with the volume and country details.
Netscout
Cyber Threat Horizon by Netscout.

Real-time DDoS events worldwide. You can filter the data by bandwidth, source, destination, event type (UDP, IPv4, DNS amplification), and event categories (Amplification, Volumetric, TCP connection). Netscout also publishes global DDoS summary
Did you like the real-time attacks map? It’s crazy. Isn’t it?


















